Database Security
Lesson Introduction• Understand the importance of securing data stored in databases
• Learn how the structured nature of data in databases impacts security mechanisms
• Understand attacks and defenses that specifically target databases
Importance of Database Security
• Why securing data stored in databases so• important and different?
• Databases store massive amounts of sensitive data
• Data has structure that influences how it is accessed
• Accessed via queries or programs written in languages like SQL (Structured Query Language)
• Transactional nature of queries (updates or reads)
• Derived data or database views
Database Threats Quiz
• Oracle, a major database vendor, sponsored a database security study which identified key security threats. In your view, which of the following is the biggest threat...Choose the best answer.
External hackers• Insiders and unauthorized users
Database Hacking Quiz
• Databases are attractive targets for hackers because...Mark all applicable answers.
They store information such as SS#, DOB etc. that can be easily monetizedThey store information about lots of users
Queries languages used to access data can be abused to gain unauthorized access.Relational Database Systems (RDBS)
• Relational model based database systems are widely used in real-world environments
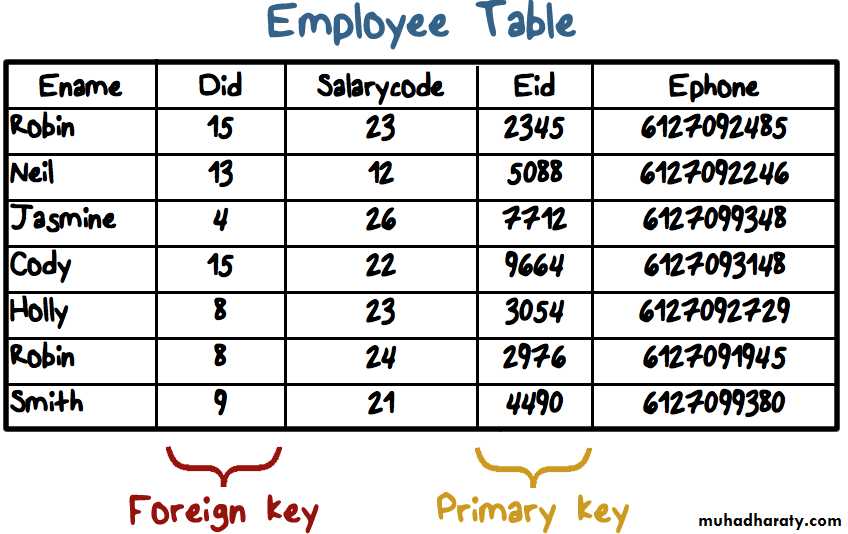
• A relational database consists of relations or tables
• A table is defined by a schema and consists of tuples
• Tuples store attribute values as defined by schema
• Keys used to access data in tuples
Relational Database Systems (RDBS)
• Operations on relations:
• Create, select, insert, update, join and delete• Example: SELECT * FROM EMPLOYEE WHERE DID = ‘15’
• It returns tuples for Robin and Cody
• Queries written in a query language (e.g., SQL) use such basic operations to access data in a database as needed.
Relational Database Systems (RDBS)
Key Value Quiz
• Two tuples (rows) in a relation can have the same primary key value.Choose the best answer:
• Yes• No
Database Views Quiz• We can use a database view to enhance data security because...
Choose the best answer.
It can exclude sensitive attributes that should not be accessible to certain usersA view can only be accessed by a single user
Database Access Control• Two commands: GRANT and REVOKE
• GRANT {privileges | role}
• [ON table]
• TO {user | role | public}
• [IDENTIFIED BY password]
• [WITH GRANT OPTION]
• Example: GRANT SELECT ON ANY TABLE TO Alice
• Privileges can be for operations such as SELECT, INSERT, UPDATE OR DELETE.
• REVOKE {privileges | role}
• [ON table]
• FROM { user | role | PUBLIC}
•
• Example: REVOKE SELECT ON ANY TABLE FROM Alice
Database Access Control
Database Access Control Quiz
• Alice has SELECT access to a table and she can propagate this access to Bob when...Choose the best answer.
Alice was granted this access with GRANT option• She can always propagate an access she has
Cascading Authorizations Quiz
• Cascading authorizations occur when an access is propagated multiple times and possibly by several users. Assume that Alice grants access to Bob who grants it further to Charlie. When Alice revokes access to Bob, should Charlie’s access be also revoked?Choose the best answer.
YesNo
DAC or MAC Quiz
• Database access control can be managed centrally by a few privileged users. This is an example of...Choose the best answer.
DAC• MAC
Attacks on Databases: SQL Injections
• Malicious SQL commands are sent to a database• Can impact both confidentiality (extraction of data) and integrity (corruption of data)
• In a web application environment, typically a script takes user input and builds an SQL query
• Web application vulnerability can be used to craft an SQL injection
• Example: Return information about items shipped to a certain city specified user in a web application that uses forms
• Script code:
• Var Shipcity;
• Shipcity = Request.form (“Shipcity”);
• Var sql = “select * from OrdersTable where
• Shipcity = ‘” + Shipcity + “‘’”;
Attacks on Databases: SQL Injections
• User enters REDMOND,• Script generates SELECT * FROM OrdersTable Where Shipcity = ‘Redmond’.
• What if user enters Redmond’ ; DROP table OrdersTable; ?
• In this case, SELECT * FROM OrdersTable WHERE Shipcity = ‘Redmond’ ; DROP OrdersTable is generated
• Malicious user is able to inject code to delete the table
• Many other code injection examples exist
SQL Injection Example
SQL Injection Defenses
• Input checking(golden rule – all input is evil)• See OWASP top 10 proactive controls at https://www.owasp.org/index.php/OWASP_Proactive_Controls
•
Login name
SQL Login Quiz• A web application script uses the following code to generate a query:
• Query = “SELECT accounts FROM users WHERE login = ‘ “ + login + “ ‘ AND pass = ‘ “ + password + “ ‘ AND pin = “ + pin; The various arguments are read from a form to generate Query.
• This query is executed to get a user’s account information when the following is provided correctly...
• Mark all applicable answers.
PasswordPIN
SQL Login Quiz #2• Query = “SELECT accounts FROM users WHERE login = ‘ “ + login + “ ‘ AND pass = ‘ “ + password + “ ‘ AND pin = “ + pin; The various arguments are read from a form to generate Query.
Choose the best answer.
• Query will fail because the provided login is not a correct userAn injection attack will result in all users’ account data being returned
If a user types “‘or 1 = 1 --” for login in the above query...
Inference Attacks on Databases
• Certain aggregate/statistical queries can be allowed by all users.• Consider a student grade database with schema studentid, student_standing (junior or senior), exam1_score, exam2_score, final_grade.
Inference Attacks on Databases
• Average score on an exam is a query that any student should be able to run.• Attacker wants to find exact score of some student.
• Inference attack when target takes the exam late
• Average score before target takes the exam
• Average score after target takes the exam
• Target score can be easily found
Inference Attacks on Databases
• Another example: only one student has junior standing in a senior class• Get average score of students who have junior standing
• This query discloses score of a single student
Defenses Against Inference Attacks
• Do not allow aggregate query results when the set of tuples selected is either too small or too large• Transform data by removing identifying information
• Deindentification
• Anonymization
• This has to be done with care
•
SQL Inference Attack Quiz
• The database that stores student exam scores allows queries that return average score for students coming from various states. Can this lead to an inference attack in this system?•
• Choose the best answer.
Yes, depending on how many students come from each state• No, it is not possible
SQL Inference Attack Quiz #2
• Assume in (1), the data in the database is de-identified by removing student id (and other information such as names). Furthermore, the field that has the state of the student is generalized by replacing it with the US region (e.g., Midwest). The generalization ensures that there are at least two students from each region. Are inference attacks still possible?Choose the best answer.
• YesNo
Database Security
Lesson Summary• Used to store lots of sensitive data that can be accessed via programs (queries)
• Access control must be based on operations allowed by databases
• New attacks on databases arise due to their unique characteristics
• Defenses must address such attacks